What is Crypto Containers and How Do They Work?
In the rapidly evolving world of digital technology, the term "Crypto Containers" has gained significant attention. These are secure spaces for storing and managing cryptocurrency keys. Expert Dr. Emily Carter states, "Crypto Containers simplify blockchain security, yet they come with their challenges." Her insight reflects a critical understanding of the dual nature of innovation in this space.
Crypto Containers utilize advanced encryption techniques. They protect digital assets from theft and unauthorized access. However, the technology is not infallible. Issues like user error and software vulnerabilities remain persistent challenges. As the adoption of cryptocurrencies grows, so does the urgency for efficient and secure storage solutions.
Despite their advantages, Crypto Containers require careful implementation. Users must understand their limitations. The balance between convenience and security is delicate. Proper education is essential to mitigate risks. As we explore Crypto Containers, it's crucial to recognize both their potential and their pitfalls. Engaging with this technology thoughtfully will help shape a more secure digital environment.
What Are Crypto Containers?
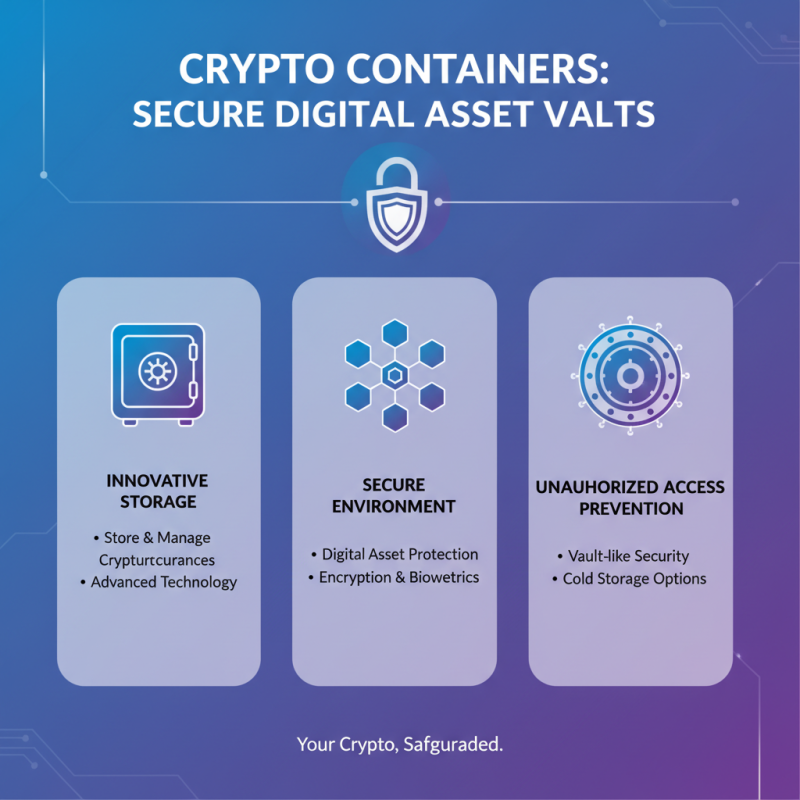
Crypto containers are innovative solutions designed to store and manage cryptocurrencies securely. They utilize advanced technology, creating a secure environment for digital assets. These containers function like vaults, keeping your crypto safe from unauthorized access.
One key aspect of crypto containers is their encryption. This technology ensures that data remains confidential and protected. The design typically includes layers of security, which help minimize risks associated with hacks or theft. Users can access their assets with secure keys, adding an extra layer of protection.
**Tip:** Always keep your keys safe. Losing them means losing access to your assets.
While crypto containers offer strong security, they are not foolproof. Users must remain vigilant. Some may overlook regular updates, which can lead to vulnerabilities. It's essential to be proactive in maintaining security features.
**Tip:** Regularly check for software updates to enhance security.
In summary, understanding crypto containers is crucial for safeguarding digital assets. These tools are powerful when used correctly, but their effectiveness relies on user awareness and maintenance.
Key Features of Crypto Containers

Crypto containers are innovative tools designed to enhance security and efficiency in digital transactions. These containers store cryptographic keys and sensitive data in a secure environment. By isolating critical information, they minimize the risk of theft or fraud. When a transaction occurs, the container ensures that the data is only accessible to authorized parties. This structure is vital in preventing unauthorized access.
Key features of crypto containers include encryption, portability, and user-friendliness. Encryption is fundamental; it keeps your data secure. Data stored in these containers is transformed into unreadable code. Portability allows users to bring their containers anywhere. This flexibility makes it easy to manage and transfer secure data. User-friendliness is crucial too. The interfaces are intuitive, even for those not tech-savvy.
However, there are challenges to consider. Users might overlook the importance of updating software. Neglecting security patches can leave vulnerabilities. Additionally, users sometimes skip backup processes. This can lead to data loss. These points highlight that while crypto containers offer robust security, users must remain vigilant. Awareness and proactive management are essential for maximizing their benefits.
How Crypto Containers Function
Crypto containers represent a transformative approach to managing digital assets. At their core, these containers bundle cryptocurrencies in a secure and portable manner. They function by encrypting data and transactions, ensuring that assets are safeguarded against theft. User accessibility is crucial, and many interfaces are designed with simplicity in mind.
According to the latest industry reports, nearly 40% of crypto users prefer managed solutions like crypto containers. This preference indicates a shift towards security over direct ownership. However, not all solutions are foolproof. Many existing containers have been scrutinized for vulnerabilities, and some offer limited recovery options if access is lost. Users must weigh convenience against potential risks.
The flexible nature of crypto containers allows transactions across various platforms. Yet, this flexibility can introduce complexities. A recent survey revealed that more than 30% of users find cross-platform compatibility challenging. As security and user experience evolve, ongoing enhancements are vital. Users must remain vigilant and proactive in understanding how these containers operate.
What is Crypto Containers and How Do They Work? - How Crypto Containers Function
| Dimension | Description |
|---|---|
| Container Type | Lightweight and portable environments for applications. |
| Technology | Uses containerization technology to isolate applications. |
| Functionality | Enables efficient management of dependencies and runtime environment. |
| Security | Provides a secure environment by isolating applications from each other. |
| Use Case | Ideal for microservices architecture and cloud-native applications. |
| Performance | Offers improved performance compared to traditional virtual machines. |
Benefits of Using Crypto Containers
Crypto containers offer several benefits that enhance security and efficiency. They package sensitive data with encryption, shielding it from unauthorized access. This method creates a secure environment for transactions and data storage. Users appreciate that their information stays safe even in potentially risky situations.
Another notable advantage is scalability. Crypto containers allow businesses to scale operations without compromising security. As companies grow, they may handle more data and transactions. Crypto containers can adapt to these changes, ensuring consistent protection. However, managing this technology might require additional training and resources. This could pose challenges for smaller organizations.
These containers also promote better collaboration among teams. Different departments can access shared resources securely without exposing sensitive information. Yet, organizations must maintain strict access controls. Balancing accessibility and security demands a thoughtful approach, which may not always be easy.
Benefits of Using Crypto Containers
Applications of Crypto Containers in the Blockchain Network
Crypto containers offer unique solutions in the blockchain landscape. Their applications span across various sectors. For instance, in supply chain management, they enhance transparency and traceability. According to recent reports, over 60% of companies utilizing blockchain in their supply chains reported improved efficiency.
Another significant application is in digital identity management. Crypto containers help secure personal data on the blockchain, reducing the risk of identity theft. A study indicated that 40% of companies face regulatory issues due to inadequate data protection. The efficient use of crypto containers can mitigate these risks.
However, the implementation still faces challenges. Many organizations lack proper understanding. Training staff on crypto container technology remains crucial. Inefficiencies in operation can arise from poorly executed deployments. Moreover, not all blockchain platforms fully support crypto containers yet. This creates barriers to widespread adoption. Despite these hurdles, the potential benefits are compelling.
Related Posts
-
Why Container Mining Farms Are Revolutionizing Cryptocurrency Mining Efficiency
-

Top 5 Best ASIC Crypto Miners Compared: Which One Reigns Supreme?
-

Exploring Alternative Crypto Miners for Sale: Comparing Efficiency and Cost-Effectiveness in 2023
-

Top 10 Container Mining Techniques for Efficient Data Management
-

10 Essential Benefits of Bitmain Container for Your Mining Operations
-

How to Use Btc Container for Effective Cryptocurrency Storage?
